
Tunneling services, also known as “ingress-as-a-service” offers were originally designed to facilitate secure communication over untrusted networks. Over the past several years they have increasingly become tools of choice for cybercriminals. Offering a cloak of anonymity and encrypted pathways, these services have emerged as an option that allows attackers to obfuscate their activities and bypass conventional security measures. In this blog, we will explain how they work, explore the types of cyber threats they enable, and provide some mitigation strategies to fortify your defenses against them.
Ingress-as-a-service vs. reverse proxies vs. tunnel technologies
It is important to understand the difference between ingress-as-a-service, reverse proxies and tunneling technologies to properly understand their features and limitations, as well as to assess the potential security impacts from their usage.
Ingress-as-a-service platforms, exemplified by services like Ngrok, primarily focus on providing external access to internal resources without requiring complex network configurations. These services typically offer temporary URLs or domain names that route traffic to specific ports or applications hosted on local servers.
In contrast, reverse proxies like NGINX act as intermediaries between clients and servers, providing features like load balancing, caching, and SSL termination. They are more configurable and are often used in production environments to enhance performance and security.
On the other hand, tunneling technologies such as GRE (Generic Routing Encapsulation) and IPSec (Internet Protocol Security) create secure pathways for data transmission over untrusted networks. While they can also facilitate external access to internal resources, they are primarily designed for establishing secure connections between networks or hosts and encrypting data in transit.
Each of these technologies serves distinct purposes and should be chosen based on the specific requirements of the network architecture and security needs.
How Do Tunnel Services Work?
Tunneling or Ingress as a Service services such as ngrok, LocalXpose, and Pinggy, provide a secure way to expose local servers behind NAT (Network Address Translation) and firewalls to the public Internet. They create a tunnel between a user’s machine and a publicly accessible endpoint, allowing for secure communication between the two. This facilitates testing and sharing of services hosted on local machines without the need to register domain names, acquire web hosting services, or go through complex network configurations.
Here’s how the process typically works with a service like Ngrok as “service provider”, its users as “customers,” and an Internet end-user as “Internet user”:
- The customer installs a command line client software provided by the service provider on their computer or server. This client software allows the service customer to customize their services;
- Upon installation, the customer must provide credentials to authenticate themselves on the service provider’s platform. These credentials are used anytime the customer requests changes to their service configurations;
- The customer uses the command line software to configure local ports and protocols to be exposed to the Internet through the service provider’s platform. For example, they can make their port TCP/3306 available to computers outside their private network through the tunneling service;
- The service provider receives the configuration request and allocates resources that may include a FQDN, protocol and port on its infrastructure;
- Traffic directed to the allocated FQDN and port over the expected protocol is automatically forwarded to the customer’s computer;
- The service provider relays data between Internet users and the customer. This traffic can be encrypted using TLS, for example, depending on the customer’s preferences;
- The real network and geographical location of the customer is hidden and never disclosed to Internet users;
- Multiple Internet users can access resources exported by the customer at the same time;
- The service provider also allows for authentication, traffic control and other fine grain configurations by the customer.
Features and Providers
The primary selling point of the commercial versions of these services . Most claim that the process only takes minutes, sometimes with no download required. Other touted features include system-generated or custom domains, support for multiple protocols, traffic and account logging, GUI or CLI interfaces, and instant SSL certificates. A free option is common, though, these usually only offer a self-expiring domain (15-60 minutes) and may have other limitations related to supported protocols and bandwidth. Paid plans are very affordable, with prices ranging from US$2.50 to $20 per month, depending on the provider and features.
A simple Google search returns results for companies both new and well-established that have entered this ingress-as-a-service market. There is also an abundance of open source do-it-yourself-hosting options. The top result for the term tunneling services is the very popular awesome-tunneling GitHub repository by user anderspitman described as “List of ngrok/Cloudflare Tunnel alternatives and other tunneling software and services. Focus on self-hosting.” The repository lists more than 60 alternatives.
What’s the point of these details? To demonstrate that the options for tunneling are so numerous and technically varied that there is no way to track or block them all. This is why understanding how these services operate is essential for effectively safeguarding networks against potential threats.
Legitimate Use Cases
Tunneling services offer a wide range of use cases across various industries and scenarios. Here are some examples:
Development and Testing: Developers can expose their work-in-progress web applications, APIs, and other services to collaborators or clients for feedback and testing without needing to deploy it to a production server.
Remote Access: Enable remote access to devices, such as cameras, IoT devices, or home servers, that are located behind firewalls or NAT routers.
Bypassing Network Restrictions: Tunneling services can bypass censorship or other restrictions by routing traffic through encrypted tunnels, allowing users to access restricted content and services securely.
Penetration Testing and Security Research: Security professionals or security research to simulate attacks, test security controls, or analyze network traffic.
File Transfer and Data Sharing: Facilitate secure file transfer and data sharing between parties by creating encrypted tunnels for transmitting files and data over the Internet.
Not-So-Legitimate Use Cases
Over the years, this tool has garnered notoriety for its role in facilitating data exfiltration, phishing, ransomware attacks, and covert communication channels. Here are some threats that can be hosted or assisted using tunnels:
Command and Control (C2) Servers: Tunnels establish secure communication channels between compromised systems and their command-and-control servers.
Phishing: Phishing websites are hosted on a bad actor’s local machine and exposed to the Internet via a tunnel.
Data Exfiltration: Tunneling services provide a secure and encrypted channel for exfiltrating sensitive data from compromised systems.
Malware Distribution: Attackers can distribute malware by hosting malicious payloads on their local machines and exposing them through a tunnel.
Current Trend: C2s Hosted by Ngrok
The inspiration for this blog was an uptick in the number of C2s found hosted at Ngrok domains (*.ngrok-free.app and * ngrok.io) since Q4 2023. The formats vary, but become easily recognizable once you have seen some of the URLs:
tcp://ed0c-2604-a880-800-10-00-bf8-8001[.]ngrok.io:18237/
tcp://ssh.6be0b042ac77[.]ngrok.io:19599/
tcp://4.tcp.eu[.]ngrok.io:11855/
tcp://mailgate.6be0b042ac77[.]ngrok.io:18335/
tcp://pop.2b287b46[.]ngrok.io:18335/
tcp://mailgate.9f50d37b[.]ngrok.io:17888/
tcp://panther-tender-ghost[.]ngrok-free.app:17888/
tcp://4118-209-105-242-243[.]ngrok-free.app:17888/
tcp://4271-1-10-161-113[.]ngrok-free.app:17888/
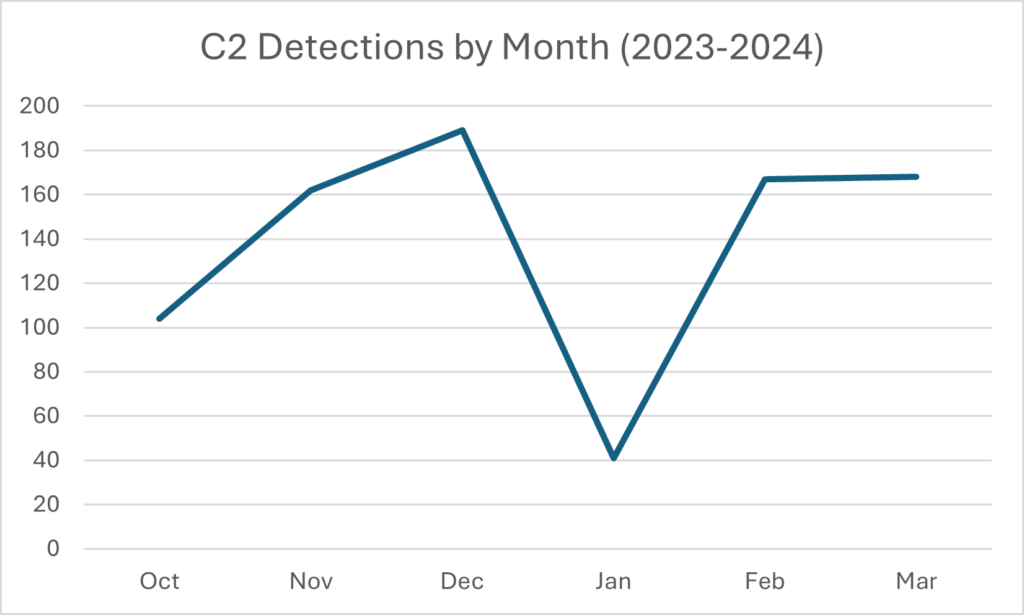
Two specific malware families collectively account for more than 96% of all observed Command and Control (C2) URLs: njRAT and Nanocore RAT. When looking at activity from October 2023 to April 2024, we noticed a significant decrease in activity in January 2024.
| Malware Family |
Percent of Ngrok C2s |
Associated Threat Actor(s), per malpedia |
| AsyncRAT | 0.23% | Various, publicly available |
| DCRAT | 0.23% | Various, sold on underground forums |
| Ghost RAT | 2.60% | EMISSARY PANDA, Hurricane Panda, Lazarus Group, Leviathan, Red Menshen, Stone Panda |
| Nanocore RAT | 29.75% | APT33, The Gorgon Group |
| njRAT | 67.08% | AQUATIC PANDA, Earth Lusca, Operation C-Major, The Gorgon Group |
| Remcos | 0.11% | APT33, The Gorgon Group, UAC-0050 |
To explore options for combatting tunneling abuse, we submitted some of these C2 URLs to Ngrok for the first time. They have a couple of options for reporting abuse:
- Via an email address found on their abuse page
- An abuse reporting API introduced on their abuse page: “If you are an institutional fraud prevention firm, we have made reporting content for removal easier and more efficient by providing a direct API integration for filing reports. If you expect to report a significant volume of abuse, please reach out to us directly to inquire about access to integrate directly with our abuse reporting API.”
Their response and subsequent removal were almost immediate. They also followed up to provide details about the API and to welcome more submissions. This speedy, proactive approach to minimizing abuse of their service was impressive and refreshing.
Tightening Your Defenses Against Tunneling Abuse
Organizations can significantly reduce the risk posed by this and similar tools when they understand how malicious actors can exploit tunneling. Protecting against this threat requires a multi-faceted approach that encompasses proactive measures and consistent monitoring:
- Network Monitoring and Analysis
-
- Implement comprehensive network monitoring to detect unusual outbound connections.
- Employ network analysis tools that can identify patterns indicative of tunneling or data exfiltration attempts. This includes sudden spikes in data transfer to unfamiliar external addresses.
- If your organization doesn’t use these services, tagging traffic or totally blocking it can be an effective measure.
- Endpoint Detection and Response (EDR)
-
- Utilize EDR solutions to detect and respond to suspicious activities on endpoints, including the unauthorized installation or execution of tunneling tools.
- Configure EDR systems to alert administrators of attempts to modify firewall settings or establish connections that are indicative of a tunneling service being used.
- Application Whitelisting
-
- Enforce application whitelisting policies to prevent the execution of unauthorized applications unless it is approved for legitimate use cases within the organization.
- Regularly update whitelists to include new legitimate tools and review the list to remove any that are no longer needed or pose a security risk.
- User Awareness and Training
-
- Educate employees about the risks associated with tunneling services and the potential for their misuse. Include information on how to recognize phishing attempts or social engineering tactics that could lead to the installation of such tools.
- Conduct regular training sessions to improve the security awareness of staff, focusing on the importance of reporting suspicious activities.
- Strict Access Controls
-
- Implement strict access controls and segment networks to limit the ability of an attacker to move laterally, even if they manage to establish a tunnel.
- Use multi-factor authentication (MFA) and strong password policies to reduce the risk of credential theft and unauthorized access to systems that could be used to deploy a tunneling tool for malicious purposes.
- Regular Security Audits and Penetration Testing
-
- Conduct regular security audits and penetration testing to identify vulnerabilities that could be exploited to install and use these tools maliciously. This should include assessments of both internal and external defenses.
- Review and update incident response plans to include procedures for detecting, isolating, and removing unauthorized tunneling services.
- Collaboration and Sharing of Threat Intelligence
-
- Participate in industry-specific threat intelligence sharing platforms to stay informed about the latest tactics, techniques, and procedures (TTPs) used by threat actors, including the misuse of tunneling services. Share insights and indicators of compromise (IoCs) related to unauthorized services use with peers and cybersecurity communities to aid in collective defense efforts.
In Conclusion
As the digital landscape continues to evolve, the abuse of tunneling services remains a persistent and evolving threat. However, by taking the time to learn about this threat, remaining vigilant, implementing robust security measures, and fostering a culture of cybersecurity awareness, businesses can safeguard their networks and data against the clandestine activities of malicious actors.
While various methods exist to counter this threat, the use of threat intelligence offers an immediate, proactive approach to detection and mitigation. IOCs can help teams swiftly identify tunneling connections and associated activity of known phishing campaigns and C2 infrastructure. For more information about Malware Patrol’s threat data feeds that cover this kind of activity, click here.
Leslie Dawn
Account Manager
Leslie Dawn is an Account Manager / Threat Intelligence Analyst at Malware Patrol. Her background of nearly a decade in cyber threat intelligence provides her with a nuanced understanding of threat landscapes and client security needs.
