Over the past 2 weeks, we saw Threat actors behind the infamous TrickBot malware have been linked to a new ransomware strain named “Diavol,â€. Also, a new malware that targets online gambling companies in China via a watering hole attack, in which visitors are tricked into downloading a malware loader disguised as a legitimate installer for well-known apps such as Adobe Flash Player or Microsoft Silverlight.
For more articles, check out our #onpatrol4malware blog.

IndigoZebra APT continues to attack Central Asia with evolving tools
Source: Research Checkpoint
Research recently discovered an ongoing spear-phishing campaign targeting the Afghan government. Further investigation revealed this campaign was a part of a long-running activity targeting other Central-Asia countries, including Kyrgyzstan and Uzbekistan, since at least 2014. Read more.

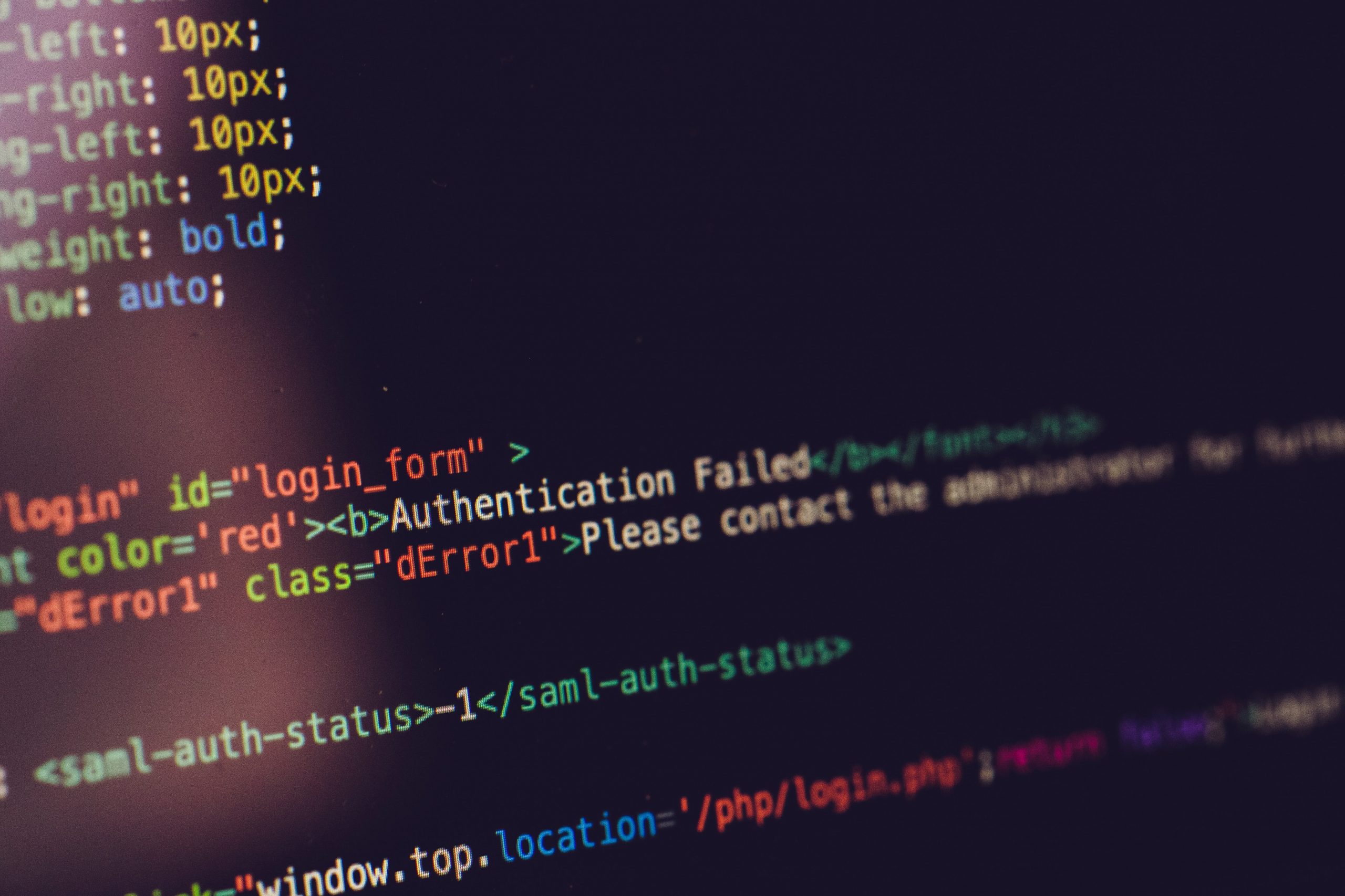
TrickBot Botnet Found Deploying A New Ransomware Called Diavol
Source: The Hacker News
Threat actors behind the infamous TrickBot malware have been linked to a new ransomware strain named “Diavol,” according to the latest research. Read more.
Lazarus campaign TTPs and evolution
Source: AT&T
AT&T Alien Labsâ„¢ has observed new activity that has been attributed to the Lazarus adversary group potentially targeting engineering job candidates and/or employees in classified engineering roles within the U.S. and Europe. Read more.

Bandidos at large: A spying campaign in Latin America
Source: WeLiveSecurity
In 2021 we detected an ongoing campaign targeting corporate networks in Spanish-speaking countries, with 90% of the detections in Venezuela. Read more.

Use of Common Malware in Operation Targeting Energy Sector Makes Attribution Difficult
Source: Security Week
Researchers at cybersecurity firm Intezer have been monitoring a campaign that appears to be mainly aimed at the energy sector, but attribution to a known threat group is made difficult by the fact that the operation involves several common malware families. Read more.

BIOPASS RAT: New Malware Sniffs Victims via Live Streaming
Source: TrendMicro
We discovered a new malware that targets online gambling companies in China via a watering hole attack, in which visitors are tricked into downloading a malware loader disguised as a legitimate installer for well-known apps such as Adobe Flash Player or Microsoft Silverlight. Read more.

LuminousMoth APT: Sweeping attacks for the chosen few
Source: SecureList
APT actors are known for the frequently targeted nature of their attacks. Typically, they will handpick a set of targets that in turn are handled with almost surgical precision, with infection vectors, malicious implants, and payloads being tailored to the victims’ identities or environment. Read more.
