PHISHING THREAT INTELLIGENCE
Real-Time Signals to Enrich Your Detection Stack
Phishing: A Persistent Threat
Phishing remains one of the most pervasive and damaging cyber threats. For years, it has been a primary method used by cybercriminals to steal credentials, distribute malware, and deliver ransomware. In fact, industry statistics claim that phishing is responsible for upwards of 90% of data breaches, making it a top concern for security teams across industries.
Modern phishing attacks have grown increasingly sophisticated. Spoofed email addresses, tailored and convincing messaging, and links to realistic-looking websites are all common tactics. Combined with advanced social engineering techniques, these campaigns can deceive even well-trained security professionals.
Our phishing threat intelligence is designed to help organizations detect and mitigate these threats before they cause harm. We aggregate phishing URLs from diverse sources, such as crawlers, spam traps, and threat-sharing partners, to maintain comprehensive and current coverage. Each indicator is evaluated through a rigorous process that combines both automated analysis and human review. This reduces false positives and improves detection of techniques that evade machine-only systems.
Expanded Intelligence for Training Humans and Machines
For organizations aiming to improve their defenses against phishing attacks through smarter detection mechanisms, rule-based filtering, or user education, we offer two powerful optional add-ons that significantly enrich our phishing intelligence feed:
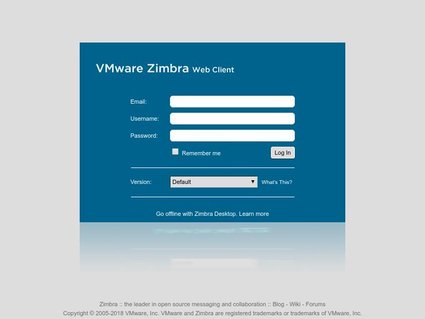
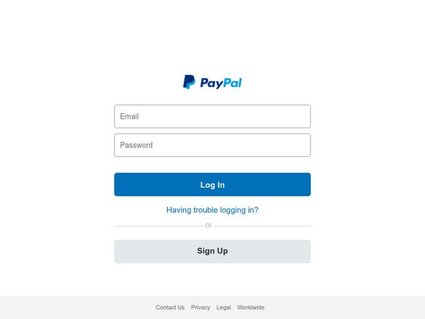
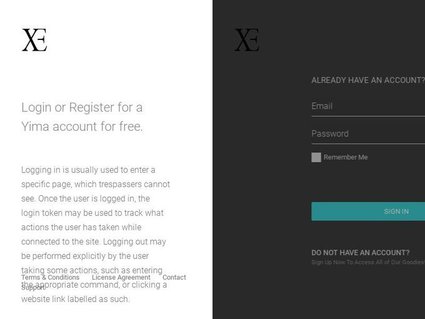
1. Screenshots and Perceptual Hashing
We capture JPEG screenshots of phishing websites and generate the corresponding perceptual hashes (pHashes) to create a visual fingerprint of each site. This capability enables multiple practical applications:
-
AI/ML Training Datasets: These images serve as labeled data for training machine learning models that analyze visual patterns in web content, supporting efforts to automatically identify suspicious or deceptive websites.
-
Phishing Simulation and Awareness Campaigns: Visual samples can be used in internal security training programs to help employees recognize phishing tactics by observing real-world examples, rather than abstract descriptions.
-
Duplicate Detection & Campaign Tracking: Perceptual hashes make it possible to identify visually similar phishing sites even when URLs and underlying code differ. This supports early detection of phishing campaigns that replicate templates across multiple domains.
2. Raw HTML Content
Our data feed includes the complete HTML source code of phishing sites. This raw data is invaluable for:
-
-
Email & Web Filter Rule Creation: Security teams can extract indicators such as embedded URLs, JavaScript patterns, obfuscated code snippets, and malicious form elements to build custom detection signatures for secure email gateways (SEGs), web proxies, and intrusion prevention systems (IPS).
-
Threat Research and Reverse Engineering: Analysts can examine and reverse-engineer phishing site behaviors to understand attacker tactics, techniques, and procedures (TTPs).
-
Security Awareness Using Real Examples: HTML samples can be sanitized and integrated into sandboxed environments or screenshots to create interactive security training modules based on current threats.
-
Model Enhancement: The structural and behavioral patterns in the HTML code are valuable inputs for training Natural Language Processing (NLP) and heuristic-based anti-phishing models.
-
Together, these add-ons transform raw phishing data into actionable intelligence for a range of cybersecurity initiatives, from advanced threat detection to employee education, to enhance an organization’s overall resilience against phishing attacks.
Feed Details
CONTENTS
– Phishing URLs, with industry classification, for 300+ international brands
Optional add-ons:
– Image bank of phishing screenshots & perceptual hashes
– Raw HTML content of phishing websites
FORMATS
– JSON
– Other formats available upon request
FEATURES
– Free evaluation
– Hourly updates
– Full-use commercial license